
The ad manager scam: how hackers steal information, money, and pages on Facebook
Various users from different countries, including Bangladesh, have fallen prey to hackers on the social media platform Facebook, who are taking control of their pages. These hackers lure users with deceptive downloads, posing as fake Facebook Ad Managers or Google Ads AI tools. However, these downloads actually install harmful malware on users’ devices, ultimately leading to the hacking of their accounts. This malicious scheme primarily targets page admins and digital marketers who use the platform for advertising, enabling hackers to access reserved funds for advertisements and steal personal information.
Dismislab examined 58 Facebook pages in the past two months, analysing their content, posts, comments, and associated websites to understand the nature, objectives, methods, financial incentives as well as origins of this scam. The study reveals that this deceptive campaign originates from the Philippines and Vietnam and has affected users from various countries, including Bangladesh.
With the help of a digital security expert, Dismislab examined the links found on the affected pages, carefully accessing and downloading the associated files to thoroughly analyse the security risks they pose and investigate the malware’s operations.
The hackers employ sophisticated hacking techniques. They create a website using keywords related to meta, Ad Manager, Google Ads, or AI to make the URL appear trustworthy. Subsequently, they either open new Facebook pages or hack existing ones, changing their names, and share the website’s link on Facebook to spread their deception.
Once users visit the website, they are presented with a seemingly innocent download link. However, upon clicking and downloading the file, the malware starts gathering personal information, including passwords, from the user’s device. In some cases, the malware may also display unwanted advertisements on their device. By disabling the computer’s firewall, hackers can potentially install other necessary malware. With the stolen login information, the hackers take control of the user’s Facebook page and use it to spread malicious posts.
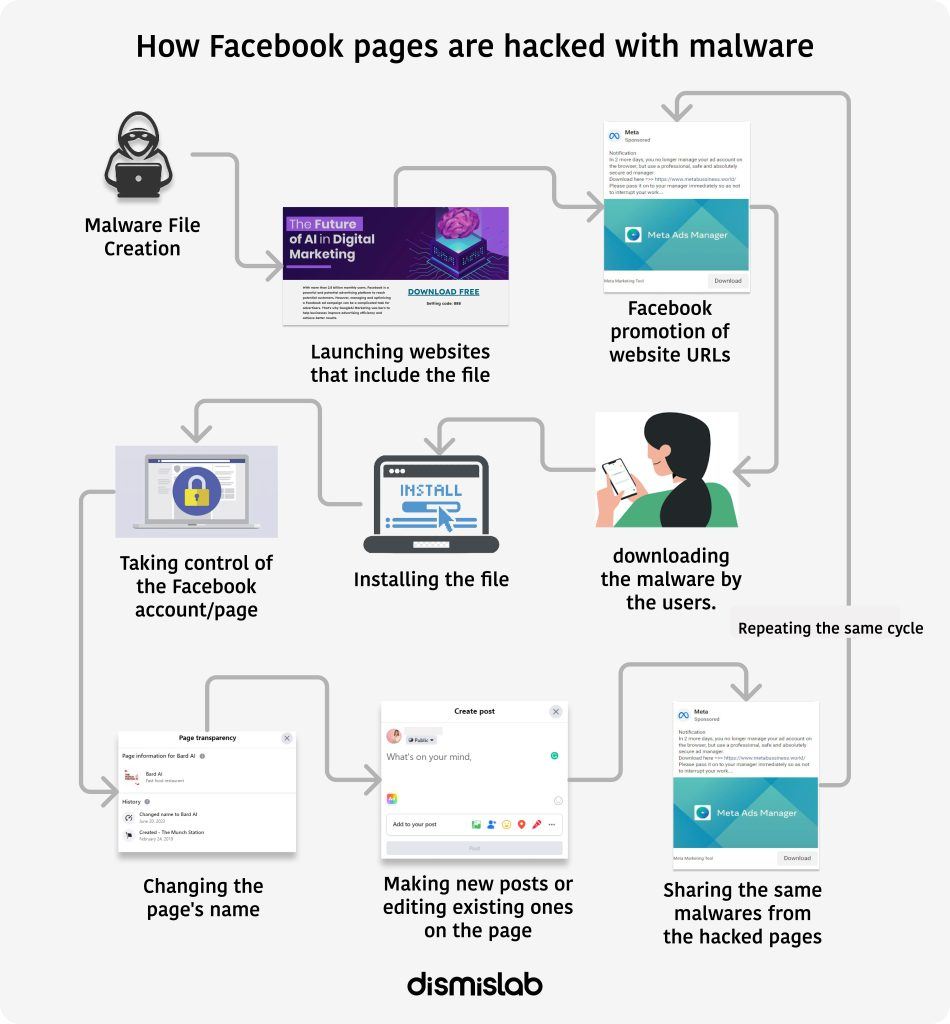
Experts indicate that this is a financially motivated scheme. After hacking Facebook pages, hackers seize financial information and exploit advertising funds from the Business Manager, use others’ money to promote their malicious posts, install harmful adware on users’ devices to generate income from advertisements, and sell users’ information to third parties. The primary targets are admins of large Facebook pages that primarily advertise products or services.
Falling on The Prey
A notable victim of hacking is the Bangladeshi publisher Adarsha. Its verified Facebook page is known for sharing information about books, related discussions, and book advertisements. On June 21st, the organisation’s founder, Mahabub Rahman, received a notification stating that he had been removed from the admin list, realising that the page had been hacked.
“In our office, we came across a clever advertisement related to Google Ads on Facebook. It had a link to Google’s website. The impression was that since the ad was Google-related and linked to Google-site, it seemed trustworthy. However, upon clicking that link and downloading the content, they managed to gain control over the page, changing the page’s link and nickname,” said Mahabub.

The image above shows the current status of Adarsha’s Facebook page, where the cover photo has been changed, and the nickname updated to “Meta Business Manager.” The page description now includes the address of Meta’s official website instead of Adarsha’s. Since the hack, the hackers have been continuously posting on this page, editing existing posts made by Adarsha, completely changing their content to suit their agenda.
The hackers’ post reads: “You won’t be able to create and edit ads in your web browser for the next 2 days. The new Ads Manager is developed safely and professionally for users. Every year, hundreds of thousands of accounts are reported stolen on ordinary web browsers. Therefore, we recommend that advertisers switch to the new browser immediately here:”

Facebook authorities, during the research, removed the hackers’ posts and links. The hackers had posted three website links on the page: manager-tools.store, manager-tools.site, and manager-tools.online, which were accessible until June. However, as of the report writing, Adarsha had not regained control of their page.
Another Bangladeshi user fell into a similar trap after clicking on a link. She reported on the “E-commerce Association of Bangladesh (ECAB)” Facebook group that she had clicked on what she thought was an update for Facebook Ads Manager, leading to her page getting hacked. In the screenshots she shared, it was evident that the hackers posted links, along with misleading ads, from the so-called “Ads Manager.”

The Facebook page of a Bangladeshi restaurant has also fallen victim to a malicious Google Bard campaign, resulting in a hack that led to its name being changed from “The Munch Station” to “Bard AI.” Later, the page owners were able to regain control of their page. But they have been unable to revert the page name back to its original “The Munch Station.”
Ganpoka, a page with nearly 52 thousand followers, was a hub for music lovers, sharing various songs and albums. The hackers took control of the page and renamed it to “Meta Business Support,” editing some of its popular posts and inserting deceptive ads for the Ads Manager. One of the first sponsored contents related to the hackers’ malicious campaign was discovered in Ganpoka during the early stages of the research.
Similarly, a Facebook page of Nigerian “Oil and Gas Free Zone Authority” fell victim to the same Google Bird advertisement scam. Although the hackers’ ads were no longer functional, they were still present on the page. A Chinese and a Pakistani individual also confirmed that they had lost control of their pages.
Facebook Ads Manager is a tool that allows users to manage and monitor advertisements on their Facebook and Instagram accounts. On the other hand, Google Bird is an artificial intelligence chatbot.
Dismislab independently verified that Facebook did not introduce any new Ad Manager service, and the existing Ad Manager was still operational, contrary to what the hackers claimed in their posts. Similarly, using Google Bird on a PC did not require any file downloads, debunking the claim made by the hackers. MyGoPen, a Taiwanese fact-checking organisation, also highlighted the falseness of the claims regarding the so-called new version of Google Bird.
Hacking Techniques
In this research, a prevalent hacker tactic has been identified. Hackers are using Facebook page posts to share URLs that lead to deceptive websites. To lend credibility to their spam, they cleverly incorporate terms associated with Meta, Google Bird, or Ad Manager when registering domains and setting up these websites. Interestingly, the fake Google Bird websites are created and hosted using Google Sites, a free website builder.
Upon visiting these websites, users encounter links prompting them to download Facebook Ad Manager, Google Bird Tool, or Google Ad Manager. In most cases, these links are shortened or abbreviated, sparking discussions on the internet. The use of shortened links allows hackers to conceal the true long URLs, making it difficult to ascertain the destination in advance. Hackers also prefer short URLs as a means to disguise their malicious intentions.
Researchers have used URL un-shortening tools to reveal the genuine or original links behind each shortened URL. These links direct to legitimate and popular cloud or project management services like Trello, Google Drive, or Dropbox. The malware is usually contained within zip files or compressed folders. However, links related to Trello or cloud storage services are not immediately flagged as suspicious by virus checking tools.
According to Dismislab’s documentation of 58 Facebook pages, 62 percent of them had their names modified by the hackers. More than half of these pages displayed admin numbers and locations. Among the 32 pages with admin information available, a majority were operated from the Philippines, Vietnam, and Thailand. The Philippines had the highest number of admins.
During the study, 52 websites were identified. One of these, AdsManager. Agency, was used on six Facebook pages to run a malicious campaign. A site titled manager-ads-meta was used on four pages. Several pages were observed to use the same name with different extensions, and multiple sites shared the same download link. In many instances, the download links were different, but the download file names remained the same, suggesting a coordinated scheme.
These deceptive sites commonly featured domain names containing terms like Ads Manager, Business Support, Ad Support, Marketing Tools, GGAI (Google AI), DLBird, and Bird AI. Among them, only seven were registered with a dot-com extension, while the rest utilised low-cost or free extensions such as dot site, dot info, dot link, dot life, or dot cloud. The websites posing as fake Google Bird downloads were primarily built using Google’s free website builder, and their URLs started with sites.google.
When You Click on The Link
Download links were shared with Ashraful Haque, a digital security expert at Engage Media, an international organisation. Upon analysing each downloaded file, he observed that the hackers specifically targeted active Facebook users, especially page or group admins, with the main objective of stealing passwords and monetizing the infected device by displaying advertisements.
According to his analysis, once a user falls into the trap and installs the malware tool, several changes are made to the computer, including granting admin permissions and making registry edits. One of these changes involves the installation of a Trojan program known as PSW.Agent.BP. This Trojan’s primary function is to search for stored passwords on the computer and then send them to a predetermined destination. The malware establishes connections to the internet using two DNS (Domain Name System) connections from the infected device.

Kaspersky Lab describes Trojan-PSW as designed to steal user account information, particularly logins and passwords. It continually searches system files containing various confidential data or registry entries, sending this data to its “master” upon retrieval. PSW.Agent.BP has also been used as ransomware in some cases.
The study identified three executable (program) files on the websites, namely Meta-Verify, AdsConnect Setup, and Googlebird. These files essentially consist of Trojan malware of the PSW.Agent.BP or Win32.Trojan.Tedy type. Once activated, these Trojans can download and run other malware or adware without the user’s knowledge. Consequently, an infected device can spread the malware to other devices through removable storage.

In addition to PSW.Agent.BP, another grayware known as urltrack trojan was found in the install file. VirusTotal detected it as malicious adware.
Adware, as described by cybersecurity firm Norton, primarily aims to generate revenue through targeted advertising to computer or mobile device users. It inundates the user’s device with numerous pop-up windows displaying various types of advertisements. Furthermore, adware can significantly slow down the infected device’s performance.
How Tactics Evolve
Hacking techniques, like the ones described in this report, are not new to Facebook. In 2022, a cyber security firm named With Secure uncovered a syndicated campaign known as ‘DuckTail.’ This infostealer program, once installed on a user’s device, steals information from their browser cookies and takes over active sessions if the user is logged in to Facebook. It goes on to pilfer logins, passwords, and even two-factor authentication codes.
An intriguing aspect of this malware is its ability to hijack Facebook business accounts associated with the user’s account. According to a TechCrunch report, The hacker gains access to the business account and assigns themselves as an admin or finance editor, allowing them to manipulate the account’s financial details and transfer money to their own account or use the victim’s account for advertising.
Despite being caught, the Vietnam-based hackers behind the campaign returned in September of the previous year with improved capabilities to bypass security measures. They started embedding malware behind Excel files at this stage.
The malware examined by Dismislab shares many similarities with older versions in terms of its modus operandi. However, according to Ashraful Haque, the digital security expert, the current malwares being distributed under the guise of Ad Manager or Google Bird are more potent. These malwares not only steal browser cookies but can also download and install additional malware once activated.
In response to such threats, Facebook’s engineering team stated in May that they have been monitoring and blocking recurring DuckTail attacks originating from Vietnam for several years. Meta and other industry colleagues have escalated their enforcement actions in response.
The platforms are seen to take measures to prevent ongoing malware activities related to Ad Manager and Google Bird. Since the start of the research, Meta has removed 36 of the 58 discussed pages, and at the time of writing the report (21 June), approximately 70 percent of the opened websites have been closed or suspended.
Despite these efforts, the hacking continues, with new pages being opened almost every week, and hacked pages being used for this purpose. Hackers are now promoting similar ads in the form of videos, with at least six such videos identified in this study.
Researchers have raised questions about how such advertisements are allowed on platforms, as ultimately the platforms also profit from these.
It says a lot about @Facebook moderation tools and processes that fake #Meta pages are managing to run ads driving users to spam websites pic.twitter.com/6pLqH6Prry
— Victoire Rio | [email protected] (@riovictoire) June 5, 2023
No Recourse for Victims
Ashraful said, “If someone is infected with this malware, the first thing to do is to disconnect the computer from the internet. Then, run an antivirus scan and remove the malware.” However, exercising caution is even more crucial.
To prevent falling victim to these hacks, users should keep in mind the following precautions. Firstly, there is no need to download Meta Ad Manager or Google Bird on a PC. For mobile apps, users must verify whether the developer is Meta or Google. Secondly, it is crucial not to get confused by the deceptive posts on Facebook. Thirdly, users should be cautious of short links and refrain from downloading anything from such links.
Unfortunately, victims can seldom, if not never, recover their lost money after being hacked. While the exact number of affected users is difficult to ascertain, a recent report by HackerRead indicates that the fraudulent Ad Manager campaign has already impacted 800 individuals and businesses, resulting in a loss of USD 180,000 in advertising dollars in the United States alone.
Digital marketing agencies and large page managers are among the primary victims of these hacking attacks. For instance, digital marketer Lonnie Maysey’s account was hijacked in late 2021, and the hackers used her credit card to advertise for an online store called Happy Store. On an ordinary day, she used to spend $15,000 on various clients’ ads.
For those who haven’t suffered financial losses, the irony lies in the fact that their pages are being used to spread malware further. Once a page is lost to the hackers, it becomes challenging to reclaim it, and the recovery process may take several months. A Washington Post report revealed that the outlet’s help desk has received numerous complaints from affected users who do not know how to regain control of their Facebook pages.
Adarsha faced a similar fate, with Mahabub Rahman expressing concern, saying “My Facebook verified platform is mainly used for branding, and I use it mostly for promotion. And since the page is hacked, I am facing permanent loss in promotion. Many people may unlike the page after seeing these posts and leave.”



